Recently, some young partners have reported that their home network has always been baffled. They suspect that there is misappropriation. In addition to the so-called Wi-Fi “shareware†that has recently been exposed, it is even more worrying whether someone will secretly connect to their own network. In fact, as long as the login route, the following steps to set, you can let the guys in the network of inorganic opportunities.

Wireless network is set up to refuse search and crack
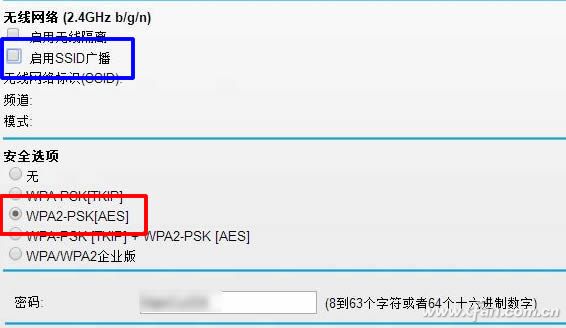
In the wireless network related page, set the encryption mode option of the password, and select the WPA2 mode and AES password encryption preferentially, which can greatly increase the difficulty of cracking the password. In addition, also in the wireless network settings page, select to turn off the SSID broadcast, mobile phones or computers will not see this wireless network when searching for available Wi-Fi, the disadvantage is that when a friend comes in or buys a new device, it must be manually Enter the cable network name to join the network, so the name should not be too complicated.
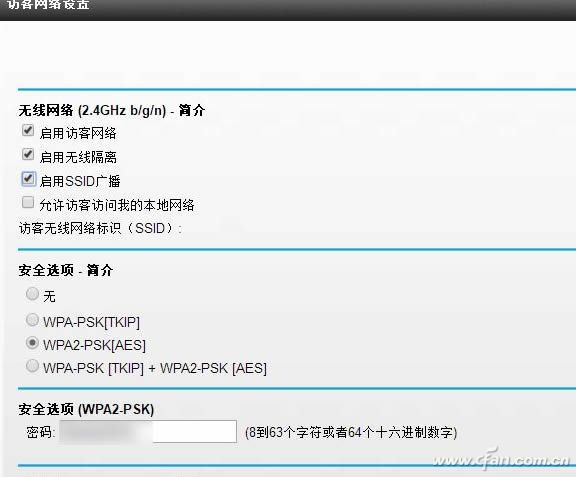
It is indifferent to the visitor's private network
Most of the newer routers provide the “Guest Network†option, which allows you to set up a wireless network for use by your guests, so that you can access the Internet, but you cannot access the routers and other devices on the network. Even stolen will not cause great losses. , can be switched off and changed at any time. Opening this feature is as simple as setting the guest network to use, setting a simpler SSID and password, and setting the SSID to display. Some routers' visitor networks can also set connection speeds, MAC authentication and access numbers, and can also be adjusted appropriately.
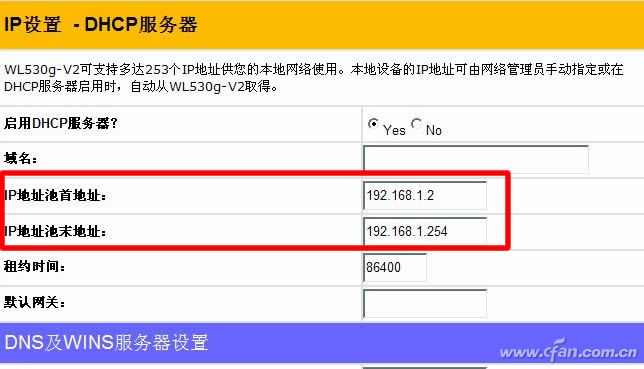
Reducing the network location of foreign equipment "self-contained"
To further improve security, you can find the DHCP settings, set the IP address (IP pool) first and last address to 192.168.1.1 to 192.168.1.20 or 30 (generally the default is 100 or even more), this can provide 20 or 30 IP addresses should be enough for families and some visitors used. However, if other people want to connect multiple devices to this network, it will be very easy to “burst†the number of IPs. This will not only limit the number of external connections, but also make it easier for us to discover externally connected devices.
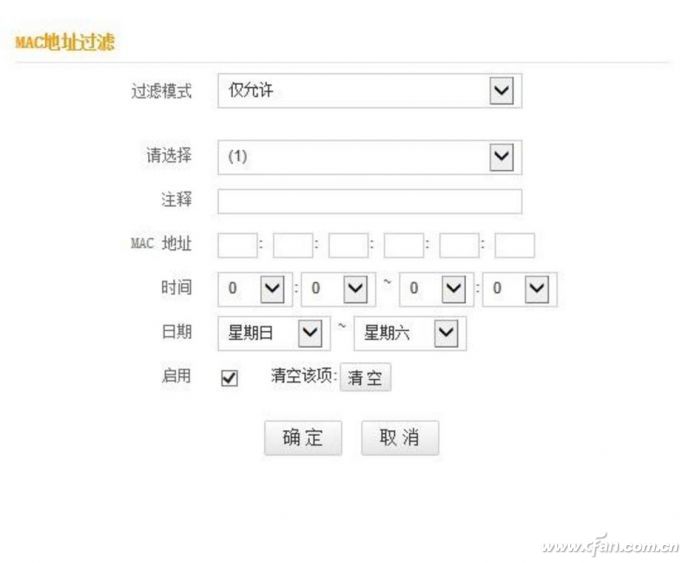
Use MAC address to let strange devices go completely
Bind MAC addresses (MAC address filtering) is the safest way to prevent outside connections, but it is slightly more troublesome. It binds the unique MAC address of the Internet device and says "dig" to strange devices so that they can't join the network at all, but their new devices must also be manually added to be used.
As for the MAC address, the mobile phone generally in the "Settings" - "System" - "About the phone" - "Status Information", pay attention to which WLAN MAC address should be seen; the computer can right click on the network icon in the lower right corner of the screen, select "Open "Network and internet settings" - "View network properties", there is a MAC address information in the open page.
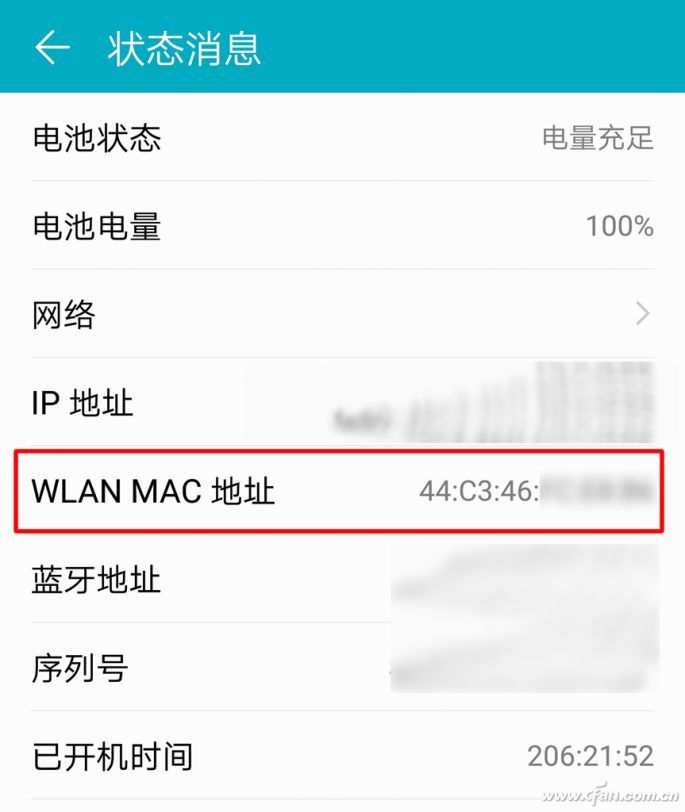
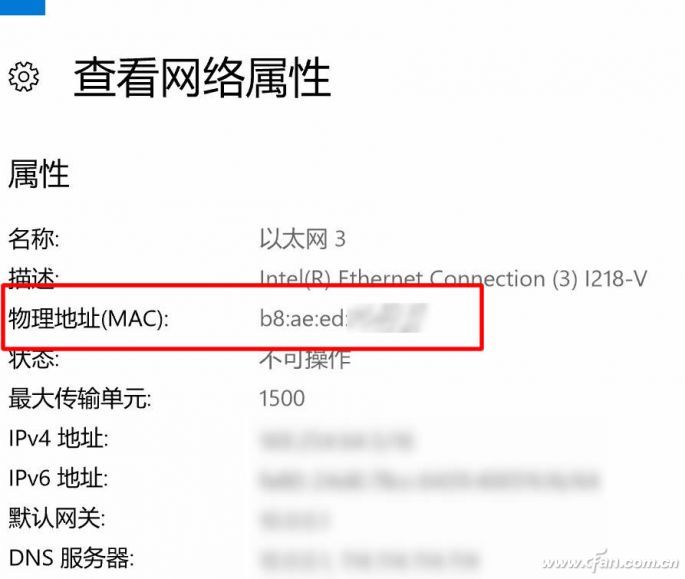
These methods have their own advantages and disadvantages. Here, we recommend that you use different combinations of situations, which can maximize the security of the wireless network, avoid the bandwidth occupied by the network, and even the problem of intrusion.

CIXI LANGUANG PHOTOELECTRIC TECHNOLOGY CO..LTD , https://www.cxblueray.com