A network based on quantum entanglement and quantum teleportation will bring a leap in network security, computing, and science.
Stephanie Wehner was a hacker before becoming a theoretical physicist. Like most fellow Chinese, she started to teach herself very early. At the age of 15, she used her savings to buy herself the first dial-up Internet modem installed in her parents' home in Wurzburg, Germany. At the age of 20, her rising popularity in the marketplace allowed her to find a job at an Internet service provider company founded by hackers in Amsterdam.
A few years later, Wehner, a cybersecurity expert, worked while studying at the university. She realized at school that quantum mechanics can provide a feature that is not available in existing computer networks-potentially invulnerable communication. Now, she has a new interest goal, she wants to transform the Internet.

Stephanie Wehner's team is trying to build a real quantum network covering Europe.
Source: Marcel Wogram for Nature
Quantum particles can be in the state of superposition-just like the cat in Schrödinger's thinking experiment can live and die-has been used to enhance data encryption for many years. However, Wehner and other researchers currently working at the Delft University of Technology in the Netherlands stated that quantum mechanics has a wider range of applications, that is, the ability to use nature to magically establish connections or create entanglement between distant objects, Realize the instant transmission of information. Wehner said that this may seem too theoretical at first, but now "people have hope to achieve this goal."
Proponents say that such a quantum Internet can open a wide range of application scenarios that cannot be achieved by classic communication methods, including connecting quantum computers together; using remotely distributed observatories to create ultra-high resolution telescopes; and even obtaining new methods for detecting gravitational waves. Some people think that the quantum Internet will replace the current Internet system in the future. Anton Zeilinger, a physicist at the University of Vienna, said: "I personally believe that most, if not all, future communications will be based on quantum." In 1997, he led one of the first experiments based on quantum teleportation.
A team in Delft has started to build the first truly quantum network, which will connect four cities in the Netherlands. The project is planned to be completed in 2020, like the quantum version of ARPANET (Advanced Research Projects Agency Network), a communications network developed by the US military in the late 1960s, which laid the foundation for today's Internet.
Wehner, who is involved in this work, is also coordinating a larger European project, the Quantum Internet Alliance, which aims to extend the Dutch experiment to the entire European continent. In the process, she and others are working hard to bring together computer scientists, engineers, and network security experts to jointly promote the design of the future quantum Internet.
At present, there are still many technical details to be explored. Some researchers caution that it is too early to evaluate what the quantum internet can bring. Wehner hopes to avoid the current weakness of the Internet from ARPANET by considering security issues in advance, "Maybe we have the opportunity to do things right from the beginning."
Quantum key
Around the 1970s, the quantum communication model was first proposed. At the time, Stephen Wiesner was also a young physicist at Columbia University in New York. He discovered the potential of one of the most fundamental principles in quantum mechanics. The principle is that measuring a parameter of a quantum system will inevitably change its state. .
Wiesner suggested that the state of an object can be used to encode information. For example, the "spin" direction of an isolated atom can be up or down, like the classic bits 0 and 1, but it can also be in both states. Such quantum information units are now generally referred to as qubits. Wiesner pointed out that since qubits cannot be measured without changing their state, this means that accurate copying or "cloning" cannot be done. Otherwise, it is only necessary to measure the corresponding clone to extract its information without changing the state of the original qubit. This limitation, later called "quantum non-cloning", has proved to be very beneficial to information security because it prevents hackers from stealing quantum information without leaving traces.
In 1984, IBM computer scientist Charles Bennett and his collaborator, Gilles Brassard of the University of Montreal in Canada, were inspired by Wiesner and came up with an ingenious method to allow two users to generate keys that cannot be cracked and only they know. This method is based on the principle that after light is polarized, light waves (electromagnetic waves) will oscillate in the horizontal or vertical plane. One user converts the randomly generated 0/1 sequence into a quantum key encoded in the above two polarization states and sends it to another user. After a series of steps, the receiver detects the key and confirms that the transmission is not disturbed by the eavesdropper's measurement. After confirming the security of the key, both parties can scramble any information composed of classic bits, such as an image, and then transmit it like any other encrypted information on the traditional Internet or any other link.
In 1989, the team led by Bennett demonstrated this "quantum key distribution" (QKD) for the first time in an experiment. Today, QKD products using similar frameworks have been commercialized, and the purchaser is usually a financial or government organization. For example, ID Quantique, established in Geneva, Switzerland in 2001, has established a quantum link that has been protecting the Swiss election results for more than a decade.
Last year, the Chinese Mozi satellite, built according to the imagination of Pan Jianwei, a physicist at the University of Science and Technology of China, achieved world-famous achievements. Mozi used a variant of the Bennett-Brassard key distribution protocol to create two keys and send one to the ground station in Beijing and the other to the ground station in Vienna. Afterwards, a satellite-based computer combines the two keys to create a new key, which is then transmitted back to the ground in a classic transmission method. The teams located in Vienna and Beijing can use their own private keys to descramble the new key (equivalent to performing subtraction with their own key), so as to obtain the other party's key. With these two keys, one team can decode the information encrypted by the other team with their keys. In September last year, Professor Pan and Zeilinger used this method to establish the first transoceanic video call encrypted with a quantum key.
A satellite like Mozi can help solve one of the biggest challenges that currently hamper quantum communication security: distance. The establishment of a key requires photons, which are absorbed by the atmosphere or optical fibers (when transmitting on the ground), making quantum transmission infeasible beyond tens of kilometers.
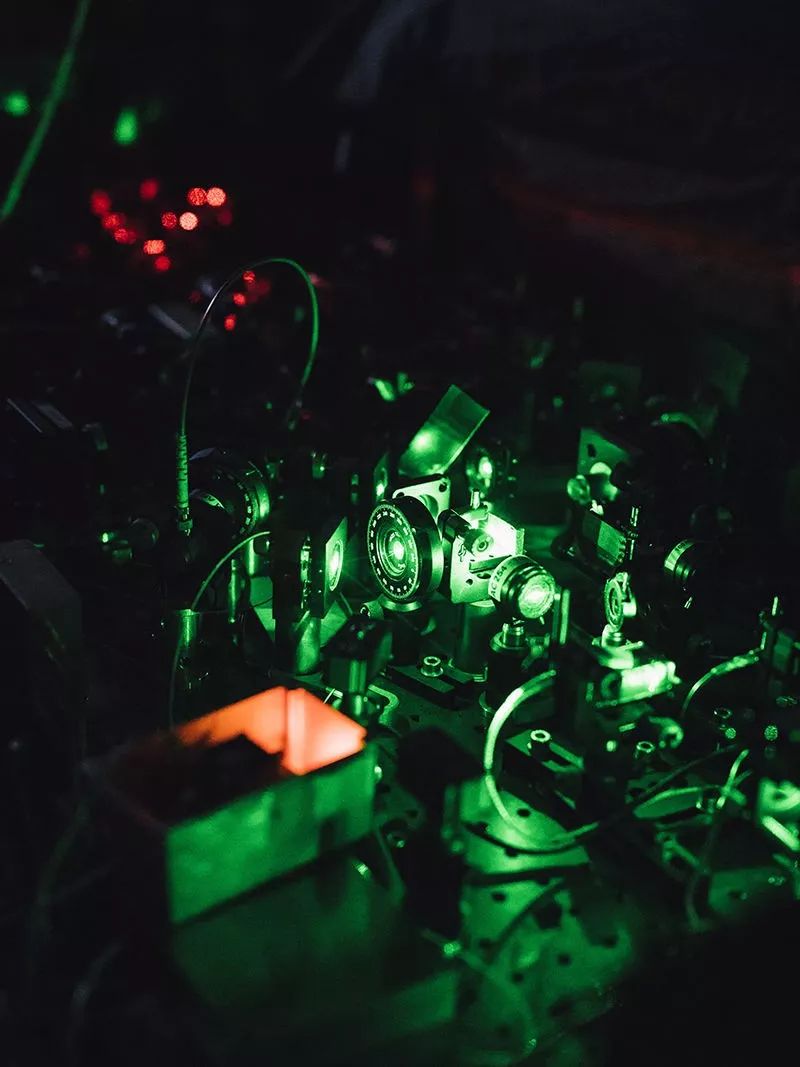
In an experiment carried out at Delft University of Technology in the Netherlands, the experimenters tried to use the diamond-based system as a quantum internet node.
Source: Marcel Wogram for Nature
Because quantum states are not replicable, it is unrealistic to want to send multiple copies of a qubit in the hope that at least one can arrive. Therefore, at present, establishing a remote QKD connection requires building a "trusted node" to act as a relay station. If someone hacks into a trusted node that handles keys in both quantum and classic forms, he will be able to copy the keys without being monitored—of course, the government or company that runs the node. This is true for trusted nodes on the ground or Mozi. "The satellite controls everything." Pan Jianwei said. But using satellites can reduce the number of trusted nodes required for remote connections.
Professor Pan said that trusted nodes represent a step closer to implementing certain applications because they reduce the number of vulnerable locations on the network. He also led the construction of a large-scale Beijing-Shanghai quantum communication trunk. The trunk line was opened in September 2017, connecting more than 4 cities with more than 2,000 kilometers of fiber and 32 trusted nodes, and is conducting tests for banking and commercial communications applications, such as connecting the data center of online shopping giant Alibaba.
Quantum connection
However, a network containing trusted nodes can only be regarded as a local quantum network. In such a network, the role played by quantum physics is limited to how nodes generate keys; subsequent encryption and transmission of information is still completely in the classic way. A true quantum network does not require the introduction of trusted nodes that are vulnerable to attack. It can also use quantum entanglement and quantum teleportation to transmit quantum information over long distances.
One of the main motivations for constructing such networks is to achieve communication between quantum computers, including cross-border communication and communication in the same computer room. The number of qubits that any computing system can carry may be limited, so connecting these systems can help physicists expand the system. "At present, the reliable prediction is that it may be possible to build a quantum computer with hundreds of qubits," said Harvard physicist Mikhail Lukin. "But if you want to exceed this scale, the only feasible solution is to use modular quantum communication. method."
In this regard, the researchers envisaged a quantum computing cloud, which contains a small number of highly sophisticated computers, and most university laboratories can access them through the quantum Internet. "It's also commendable that this kind of cloud quantum computing is also safe," said Ronald Hanson, an experimental physicist at Delft University. "The people on the server side won't know what program you are running, nor will they be able to get you in Data used. "
Researchers think of a large number of potential Internet application scenarios, such as auctions, elections, contract negotiations, and high-frequency transactions. Quantum methods will be faster and safer than traditional methods.
But it is probably science itself that is most affected by the quantum internet. Some researchers have pointed out that if quantum entangled synchronous clocks are used, the accuracy of navigation networks such as global positioning systems can be improved from meters to millimeters. Lukin et al. Proposed to use quantum entanglement to combine distant atomic clocks into a single clock with greatly improved accuracy. He cited, for example, that this is expected to bring new methods of detecting gravitational waves. In the field of astronomy, quantum networks may be able to connect optical telescopes thousands of kilometers apart to obtain a resolution equivalent to a single-disk telescope of the same diameter. This method is called very long baseline interferometry. It is already a routine application for radio astronomy, but for optical astronomy observations, the required time accuracy cannot be achieved at present.
Extraordinary security
In the past decade or so, the physicist Christopher Monroe of the University of Maryland and others have given some of the cornerstones needed to build a real quantum network through experiments, such as the use of teleportation to encode the information of qubits from a From one place to another (see "Building a Quantum Internet").
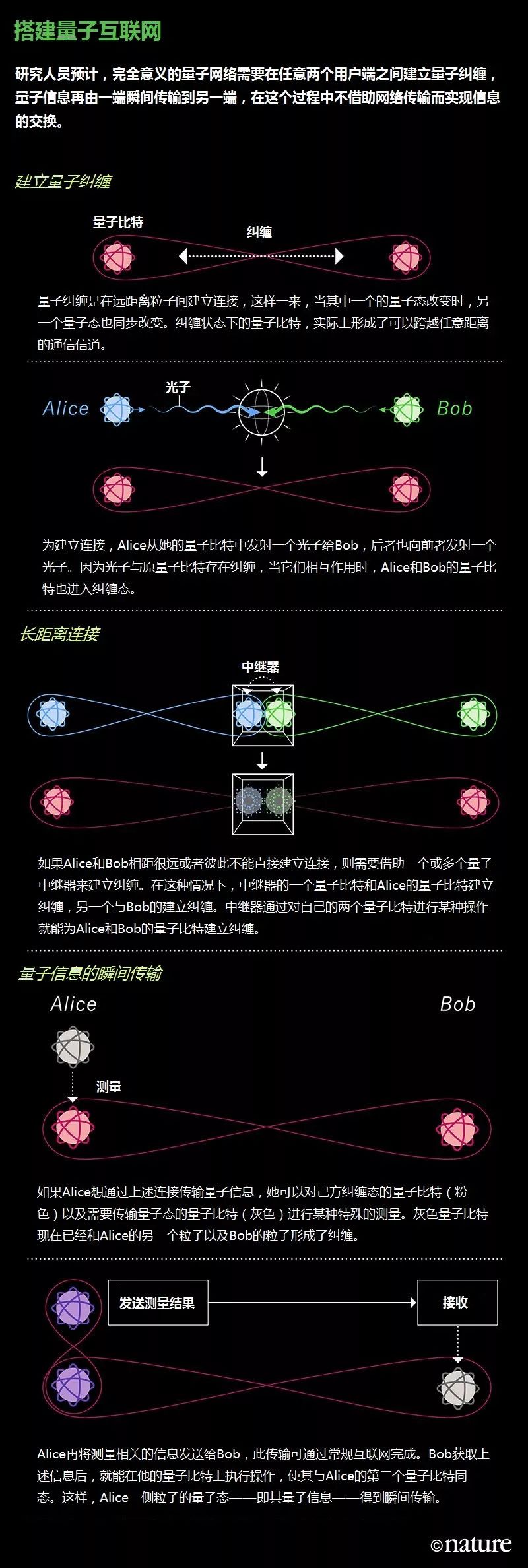
Nik Spencer / Nature
To understand how quantum teleportation (also proposed by Bennett and Brassard) works, imagine two users: Alice and Bob. Alice has a qubit (probably a trapped ion or other quantum system) and wants to transfer the information stored in it to Bob. As it happens, Alice and Bob have two "agent" particles entangled with each other-also qubits. If Alice can establish entanglement between her qubit and the proxy particle, then this qubit will also entangle with Bob's particle. To this end, Alice performs a specific type of joint measurement on her two particles, and then she shares the measurement result (regular classic data) with Bob. In order to complete the final step of teleportation, Bob manipulates his particles according to this information. Eventually, the particles can be in the same state as Alice's qubits.
In fact, it doesn't matter how Alice and Bob obtain the entangled proxy particles. These particles can be single atoms delivered through briefcases or photons emitted by third parties. (Last year, one of Mozi ’s experiments was to send entangled photon pairs to two ground stations in China, separated by more than 1,200 kilometers, a historical record.) Alice and Bob can also send photons to a third location Interact with each other to make the qubits they hold entangled.
The beauty of quantum teleportation is that quantum information does not actually spread through the network. The propagating photon is just to establish a connection between Alice and Bob in order to transmit quantum information. If one pair of entangled photons fails to establish a connection, the other pair will. This means that the loss of photons will not cause the loss of quantum information.
Connection and relay
Quantum Internet will be able to generate quantum entanglement between any two users on demand. Researchers believe this will involve sending photons over fiber optic networks and satellite links. However, connecting remote users requires a technology that can extend the reach of quantum entanglement so that entanglement can spread between users and relay stations.
In 2001, Lukin and his collaborators proposed a way to implement such a quantum repeater. In their scheme, small quantum computers that can store qubits and perform simple operations are used to establish quantum entanglement between qubits in upstream base stations and downstream base stations. Repeating this "quantum entanglement exchange" process along a path in the network can eventually establish quantum entanglement between any two users.
In 2015, Hanson and his collaborators connected two qubits caused by single-atom defects in diamond crystals-the two are 1.3 kilometers apart, showing how to build a quantum network. The photons emitted by these two qubits interact at an intermediate station and establish entanglement. MIT physicist Seth Lloyd said: "This shows that people can indeed establish entanglement between two long-range quantum information processors-strong and reliable entanglement."
Researchers are also exploring other ways to construct and manipulate qubits, including the one developed by Monroe et al., Using single ions suspended in a vacuum; or using a system that reflects paired atoms and photons back and forth through two mirrors in the cavity.
Like Hanson's diamond system, these qubits can be used both to build quantum repeaters and to make quantum computers. Fortunately, for those who wish to expand the scale of quantum communications, the requirements of repeaters may not be as demanding as the requirements of mature quantum computers. In September last year, Iordanis Kerenidis, a quantum computing researcher at the University of Diderot in Paris, made the above point of view at a quantum repeater seminar in Seefeld, Austria. "If you tell the experimenters that you need 1,000 qubits, they will laugh," he said. "If you tell them you only need 10—well, they will laugh lighter."
System engineering is related to the future of quantum internet. "From an experimental point of view, people have given various building blocks (of quantum networks)." Said Tracy Northup, a physicist at the University of Innsbruck in Austria. His team is a member of Wehner's Pan-European Quantum Internet Consortium, engaged in cavity qubit research. "But put them together-we all know how challenging that is," Northup said.
Currently, Wehner's alliance is still in its infancy and is seeking public funding and corporate partners. At the same time, Wehner, Hanson and Erwin van Zwet (a joint system engineer of the Dutch scientific organization TNO) jointly led the construction of a demonstration network. Hanson and his colleagues continue to increase the speed of the system; in the 2015 experiment, the system established a total of 245 pairs of entangled qubits in a time equivalent to about 9 days. Another key challenge is to reliably convert the light emitted by diamond qubits from visible wavelengths to longer infrared wavelengths, which can propagate better in optical fibers; this is a tricky problem because new photons still need Carry the previous quantum information, but there is no possibility of cloning. Earlier this year, Hanson and his colleagues achieved this by allowing photons to interact with longer-wavelength laser beams. This technology enables qubits separated by tens of kilometers to establish a connection through optical fibers.
Hanson's team is currently establishing links between Delft and The Hague, with a distance of 10 kilometers between the two locations. The researchers hope to connect four Dutch cities by 2020 and set up a relay station in each city. If successful, the project will be the world's first truly network based on quantum teleportation. Hanson ’s team hopes to open this network to other interested teams in the future, allowing them to conduct quantum communication experiments remotely, much like IBM ’s Quantum Experience, which allows users to log in to a primary quantum computer remotely .
The above network may provide a test platform for researchers to repair Internet defects, especially users can easily forge or steal identity. "You can access the network without creating an identity account. This problem has a long history." Robert Broberg, a network engineer at telecommunications equipment giant Cisco, said at the Seefeld seminar. The quantum technology proposed by Wehner and others allows users to prove that they have a legitimate key (a series of classic bits) without uploading a key, thereby verifying their identity. The user and server use the above key to create a qubit sequence and send it to the "black box" between them. This black box-say, a cash machine-can compare two sequences without identifying the key to confirm whether they match.
However, some researchers reminded not to over-consume the development prospects of this technology. "Today's Internet will not be fully quantized, just as computers in the future will not all use quantum computing technology." Said Nicolas Gisin, a physicist at the University of Geneva in Switzerland and co-founder of ID Quantique. Most things people hope to achieve through quantum networks can actually be done with more conventional techniques. "Sometimes, some things look wonderful at first, and it turns out that it is easy to achieve without the help of quantum effects." Norbert Lütkenhaus, a physicist at the University of Waterloo in Canada, said he is participating in formulating relevant standards for the future quantum Internet.
Zeilinger said that time will tell us whether the potential dividend of the quantum Internet can be realized. As far as we know, invisible teleportation is a phenomenon that is physically possible but does not occur naturally. "So it is indeed a new thing for humans, which may take some time to understand."
Wehner is familiar with both physics and cybersecurity, and has become a benchmark for colleagues in the industry. After completing a lot of work based on the core theory of quantum mechanics, she enjoyed the opportunity to shape these future networks. She said: "For me, this is really perfect.
40W Medical Power Supply,Medical Power Adapter,Rade Power Supplies,Isolated Power Supply Hospital
Shenzhen Longxc Power Supply Co., Ltd , https://www.longxcpower.com