The intelligent access control management system is an important part of the integrated security protection system of the intelligent building. It is a necessary prerequisite for people working and living in the intelligent building to create a safe space. Its basic function is to analyze and identify the information transmitted by the magnetic switch, the anti-theft alarm detector and the fingerprint palm recognizer, so as to effectively monitor and manage the opening and closing of the door, and ensure the free access of the authorized entry personnel. To limit the entry of unauthorized personnel, to alert the forced intrusion behavior and other abnormal situations; at the same time, store and manage information such as the entry and exit personnel code, access time, and entry location number to achieve effective retrieval of incidents or personnel. management. The final day of the intelligent access control system is to ensure the security in the protected area and realize the intelligent management of the door and the entry and exit personnel.
2. System function designAccording to the current requirements, the intelligent access control management system designed in this paper needs to implement the following basic access control functions:
(1) System management: including administrator login, change registrant password, set ODBC data source.
(2) Site management: including adding a new site, activating, deleting, emptying the site, and setting the site property.
(3) User organization management: including organization management and user management.
(4) Hand Reader Management: including adding a new Hand Reader, clearing, registering users, registering time periods, registering holidays, deleting, associating doors, setting properties.
(5) Advanced management: including setting holidays, setting time period, combination verification, administrator, data backup, manual switch door, setting real-time monitoring.
(6) Query report: including querying user information, holidays, time periods, system logs, and so on.
(7) Access control function, mainly has the following functions: flexible selection and configuration of the number of monitoring doors, naming the monitoring door; flexible setting of the automatic switching time of the door; only the identity is verified first, after the system is approved, the door can be opened; Start or disable a Hand Reader or a station, flexibly set which doors can be opened by a Hand Reader; when the system is set, some doors are set to normally open or normally closed. Normally closed door, any verification can not be opened; real-time display of all current door switches; alarm for some abnormal doors; record all doors and Hand Reader, these will be used as historical records for later query; Query and count the action of the designated door or the HandReader within a specified time period; control the opening of a certain door or all doors through the software system, mainly for special situations such as emergency evacuation.
Through the computer network management, the system can realize the functions of information resource sharing, remote monitoring and linkage of various security subsystems. It not only focuses on the improvement of overall security and reliability, but also makes the maintenance of the system easier and ensures the maintenance of the instant. Sex and effectiveness reduce system operating costs.
3. System technology designConsidering that the data of the smart access management system is distributed, it is necessary to use the appropriate technology for the system to access and share these remote data. In order to achieve system data sharing so that data flows reasonably between the various departments of the company, we can share data at the database level or share the data at the application's business logic layer, although the technology used to implement such applications and There are many solutions, but here we introduce the technical requirements for the characteristics of this system.
3.1 Distributed Technology
Different from the general information management system, the main feature of the intelligent access control system is that the distribution of data and the structure of the system determined by it will also be distributed. The usual information management system only manages local data, and the data is more concentrated. Easy to manage. However, this system still has some new features of the information management system. We use the access engine that can access data remotely when using the database access technology, which makes the system implement a similar information management structure.
This system uses J2EE's Struts+Spring+Hibernate architecture. The J2EE architecture is divided into three levels: the presentation layer (customer layer component), the business logic layer (including the Web layer component and the business logic layer component), and the enterprise information system. The architecture has cross-platform features, and the three levels in the structure can be collaboratively applied under different platforms. The fierce presentation layer can use different client programs, so it has good distribution and can adapt to the requirements of distributed management. In the background application system integration, different application systems of the enterprise can be integrated into the structure. It can effectively protect existing resources from being destroyed.
3.2 Struts+Spring+Hibernate technology
The system adopts the standard three-layer structure mode design, specifically selected Struts+Spring+Hibernate, this combination method is based on the open source framework of J2EE platform. Among them, MVC adopts Struts, business logic layer adopts Spring, and persistence layer adopts Hibernate.
Struts+Spring+Hibernate (referred to as SSH) is the mainstream application technology based on J2EE architecture of many well-known foreign software companies. By using the SSH framework, the entire framework interacts in a loosely coupled manner on each architectural layer, regardless of the underlying technical details. The intelligent access control management system uses the SSH framework, which not only enables rapid development, but also facilitates system expansion and integration with other existing systems. Figure 2 below is a schematic diagram of the combination of the entire frame:
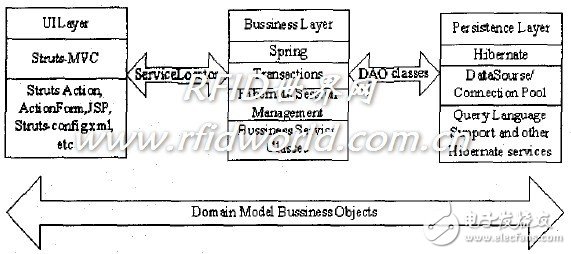
Figure 1 Struts+Spring+Hibernate framework
Hopper Or Motor,coin motor,metal coin hopper,coin hopper
Guangzhou Ruihong Electronic Technology CO.,Ltd , https://www.callegame.com