This paper analyzes the ever-changing car theft methods and the development of the corresponding car anti-theft technology. It focuses on the encryption technology and system components of TI's latest car anti-theft solution, DST+ transceiver, and describes the new generation of radio frequency compatible with it. Identification (RFID) technology solution—the three-dimensional antenna analog front-end chip implements the principle of keyless entry.
This article refers to the address: http://
Electronic anti-theft devices based on transceiver technology have become standard equipment for European motor vehicles due to consumers' pursuit of higher security. Following Europe, Canada has also issued a standard on anti-theft systems. Although the installation of anti-theft devices is currently voluntary in the United States, it is also becoming a promotional tool for car manufacturers. In addition, after the recent report on gang crimes and car theft in Japan, Japanese automakers are also facing the problem of tightening the installation of anti-theft systems for local products.
The upcoming generation of new transceivers has a special diagnostic function, that is, the authorized person can obtain the history information of the anti-theft system when reading the secret information in the key. The number of authorized spare keys in the system, the time stamp of the learning process, and other background information will be part of the transceiver's security features.
Special integrated circuits also provide other convenient features such as "keyless entry." This feature has been discussed in the automotive industry for some time. After years of technical development in automotive safety and RFID (radio frequency identification), the multi-channel antenna structure can finally be used in identification devices that consume only one battery (eg key chain, credit card). The analog front-end processor for low-frequency applications is connected to these antenna structures. The supported functions are basically independent of the direction of the device, and the antenna body is small and the power consumption is greatly reduced.
Transceiver update
The cryptographic transceiver is the second generation transceiver for the anti-theft device, almost completely replacing the first generation of read-only transceivers. One example is TI's Digital Signature Transceiver (DST), whose query/response technology ensures maximum security. The third-generation transceiver is working to match the remote keyless entry function with the anti-theft transceiver function to reduce the associated costs.
So far, from the analysis of vehicle theft situation, it can be judged that the transceiver has not been decrypted, which confirms that the current automotive market has reached a high safety standard. The focus now is on how to prevent fraud associated with theft of vehicles.
Through careful study, the following methods of stealing related to transceivers can be easily summarized:
Copy the spare key. A dishonest driver can lie about losing the key and asking the car dealer for a new key. Suppose that when the car is initially bought, the driver gets three keys, and he can get a total of five keys by pretending to report the loss twice. They look exactly the same and both contain a valid transceiver. As with buying a car, the system still only accepts 3 keys. In this way, the driver can hand over the two keys that are valid to the criminal associates, and present the other three to the insurance company, so that others think that the anti-theft system has been cracked.
Some automotive manufacturers have a central database to track spare keys. One of the advantages is that even if the car is stolen, information about the total number of spare keys and keys can be obtained. Use this information to get an idea of ​​the total number of original and spare keys. However, maintaining such a central database requires high costs and data networks, so most car manufacturers are discouraged. DST+ is TI's fourth-generation transceiver, which stores historical and diagnostic data in each key, allowing automakers to avoid investing in building and maintaining a central database.
When you rent a car, you can do it. After renting the car, copy a few mechanical keys, remove the transceiver from the original key, and stick it near the electronic lock antenna (such as under the dashboard). In this way, the electronic lock can always detect the "effective" transceiver signal, because the car can be opened only by the mechanical key, so it is easy to steal in the future.
This poses a challenge for key manufacturers who must develop new ways to assemble the car key and transceiver so that the transceiver cannot be removed without breaking the key or its function.
A more advanced means of car theft is also related to the look-up of the watch. Assuming that the key can be owned in a matter of days or hours, advanced professional engineering equipment can be used to send an inquiry signal to the transceiver and read its response, creating a database to store responses to different queries. Then, the thief can obtain the correct response of the electronic anti-theft device to the inquiry signal through the database, and then at least emit a query signal that can obtain a correct response to open the car. However, the success rate of this approach is low.
DST+ provides a mutual authentication process that ensures that the transceiver does not respond to any inquiry signals. The transceiver verifies that the request signal is from an authorized active base station, so the method of checking the car will have no effect.
Fourth generation transceiver
The new generation of transceivers focuses on car history tracking, post-burglary diagnosis, prevention of "watching" car theft, and storage space for larger data or car data.
A dedicated memory area protected by a special password in the transceiver allows the seller (such as a car manufacturer) to get background information about the car key and the security system. Its characteristics are as follows:
Display the date and time stamp of the learning process;
A non-resettable step counter that tracks the total number of car keys the system has learned;
The identification code of the car.
The special learning process for new car keys allows car manufacturers to obtain information about the safety system from the car key without having to enter the car safety system or use a central database. This makes it possible to implement two functions: 1. Detecting whether the car key is still valid for the security system, preventing the use of invalid keys for fraudulent activities; 2. Identifying the key that has been disabled by the security system and reinserting the keyhole and attempting to start the engine . This information will be encoded and stored in a dedicated "anti-theft byte".

The above functions are supported by the mutual authentication protocol of the transceiver. As mentioned earlier, this security mechanism denies access to unauthorized base stations. This technology, combined with a sophisticated key-level system dedicated to vehicle safety, ensures that only authorized departments can read confidential data.
New generation keyless entry system
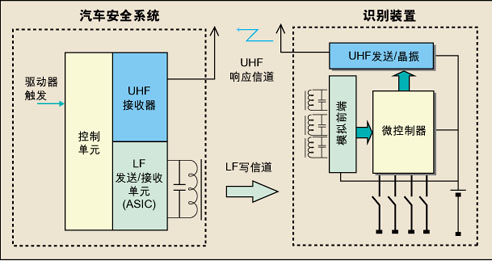
To develop a car without a mechanical key, first develop a keyless entry system. The new generation of keyless entry systems differs from previous remote keyless entry systems in that they automatically recognize the driver and unlock the lock when the user approaches or touches the door handle. Radio frequency identification (RFID) technology can achieve this convenience and ensure that the system can correctly identify the driver under all circumstances. An identifier (usually a keychain or credit card shaped device) carried by the driver with one or more antennas connected to the RFID device. The base station antennas are coupled to these antennas to provide magnetic field energy to nearby identification devices (eg, 50 cm areas) for battery-free standby functions. In the long range (e.g., 200 cm), the antenna in the identification device receives the data amplified and processed by the base station. Figure 1 shows a block diagram of a keyless entry system using TI's 3D Antenna Analog Front End (3D AFE).
The magnetic field generated by the magnetic loop antenna causes a well-known field distribution and forms a well coupled and completely uncoupled region between the base station antenna and the identification device antenna. Of course, there is no data and energy transfer in the uncoupled area. Since the position of the identification device of the keyless entry system in the magnetic field is random, measures must be taken to minimize the extent of this area.
The generation of a rotating magnetic field by a base station is a solution, and the rotating magnetic field can be generated by an orthogonal antenna. However, this method is complicated and often limited by the small space of the antenna in the car. Another alternative is simpler, using a three-dimensional antenna to simulate a front-end chip, such as the TMS37122. The chip demodulates signals from up to three antennas and, if placed orthogonally, demodulates data from the three coordinates x, y, and z. Thus, even if the base station antenna in the car is a simple and economical loop antenna, the area without coupling can be minimized. Regardless of the direction in which the identification device in the magnetic field is facing, there is always one antenna that can receive a sufficiently strong signal to cover the desired operating range. In addition, an external microcontroller processes the relevant protocol and responds to the Ultra High Frequency (UHF) identity query signal received by the three antennas.
Figure 2 is a block diagram of the three-dimensional antenna analog front-end chip - TMS37122. As shown, the TMS37122 can be connected to up to three low quality factor antenna circuits. All three antennas can receive low frequency signals from 125 kHz to 135 kHz, with one antenna channel (RF1) providing modulation. This antenna utilizes frequency shift keying (FSK) technology to transmit low frequency data and is therefore compatible with existing transceiver modulation techniques. This modulation function is often used in a battery-free backup mode. When the key battery power is insufficient, the base station supplies energy to the identification device through the magnetic field.
A low frequency carrier signal above a certain threshold triggers an internal control unit to detect three input channels RX1, RX2 and RX3. A special protocol enables the combination/selection of the channel RXi and ensures improved performance over a wide operating range.
After the internal trigger, the control unit constantly monitors the RF signal representing the awake mode, and only sends a wake-up signal to the external microcontroller when receiving the awake mode signal stored in the EEPROM of the device, and then transmits the demodulated data to the micro Controller. In addition, recovering the carrier clock signal can be used as a time reference for microcontroller measurements, which minimizes the power consumption of the backup power supply.
One of the key issues in the keyless entry system is to detect the position of the transceiver, especially whether it is inside or outside the vehicle. The TMS37122 device provides sophisticated built-in features to solve this problem.
Summary of this article
Since the introduction of the electronic lock in 1993, the market for automotive RFID transceivers has grown rapidly. Today, the growth of both security and convenience has driven new developments in this market and continues to present new challenges to RFID providers. With the introduction of cryptography and the integration with remote keyless entry, fourth-generation transceivers have been born.
With the success of the keyless entry system in the market and its widespread use in low-end cars, there is a versatile IC solution that can connect up to three antennas, which handles all protocols and is fully compatible with fourth-generation transceiver technology. And it reduces costs while improving safety.
Gasoline Generator,Fule Tank Generator Set,Silent Trailer Diesel Generator,Small Diesel Power Generator
XCMG E-Commerce Inc. , https://www.xcmg-generator.com