Access control, also known as the access control system, is a digital management system for managers to enter and exit. At present, with the development of industrial automation and the increasing demand for applications, access control systems have been used more and more, but the traditional access control system generally adopts the implementation of access control and video picture recording separation. This brings a lot of inconvenience to the field wiring, and its cost will be greatly improved. The ARM9 and Linux-based embedded access control system mentioned in the scheme integrates the access control and picture recording functions, and describes the software design of the system in detail. The access control system uses the B/S software architecture, uses the embedded server boaserver, combines CGI technology, embedded database and embedded graphics library to realize the requirements of the access control system.
1 System working principle and composition1.1 How the system works
The access control monitoring system adopts B/S architecture (Browser/Server, browser/server mode). The access control monitoring system based on B/S architecture is firstly an access controller with Ethernet interface. Secondly, the access controller is built-in. Ethernet TCP/IP protocol and WEB service program; when the system is connected, the user can regard the access controller as a computer with a broadband network interface and directly connect it to the network switch. When the user manages the access control, there is no need to install any additional software, and the management of the access control system can be realized directly through the browser, and the operation is convenient and concise.
1.2 System components
As shown in Figure 1, the system server is composed of an ARM9-based access controller, card reader, electric lock, front-end camera, etc. When a person enters and exits the door, the card reader can sense the card and the card. The information is sent to the access controller, and the access controller performs card legality check. By reading the user database, it is checked whether the card number has corresponding cardholder information, and if so, the corresponding permission information of the card is checked, and everything matches. After success, decide whether to open the door. This ensures the security of the system. At this time, the operation performed by the access controller also has an image recording operation, that is, the camera is recorded through the front camera at the same time as the door opening operation, and transmitted to the corresponding storage device for the user to access.
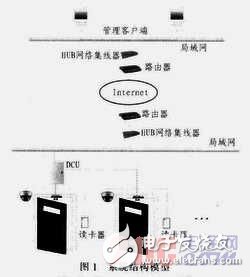
The client can remotely access the access controller, that is, the server, and the corresponding authority operation through the browser, and can realize user information input and authorization management, hardware setting, access image monitoring, door opening, data browsing and the like. Figure 1 shows the system structure model.
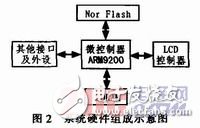
2 access controller hardware designThis system uses ATMEL's AT91RM9200 (hereafter referred to as 9200) as the MCU. The processor is based on the ARM920T core, with a working frequency of 180MHz and a performance of 200 MI/S. The system uses open source LINUX OS. The kernel version is 2.6.25, the system uses 1 piece of Nor-Flash, the capacity is 64 MB, 2 pieces of SDRAM, and the capacity is 32 MB. As shown in Figure 2, the access controller is based on the ARM9200. At the same time, there is also an LCD controller connected to the display for user debugging. In addition, this access control system can connect up to 256 card readers and corresponding cameras. The system hardware composition diagram is shown as in Fig. 2.
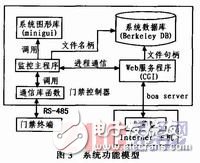
The whole system is divided into two parts: front and back. The background monitoring program will monitor whether the card reader has card swiping information and respond to the card swiping information. The foreground responds to the client access request by calling the CGI server program through the boa server. The system function model is shown in Figure 3.
3.1 Front desk design
The system front-end is mainly composed of a boa server server running on the access controller and a CGI service program. The boa server will always monitor whether there is remote user access. When a client access request arrives, the boa server configuration file is sent to the corresponding directory. The corresponding CGI service program is called, and after the processing is completed, the boa server returns the processing result to the client.
3.1.1 Introduction to CGI and how it works
The full name of CGI is the "Colnnlon Gateway Interface", a program method based on browser input and running on a web server.
CGI works by first asking the browser to refer to the URL of a CGI application via an HTML form or hyperlink request. After receiving the request, the server executes the specified CGI application. The CGI application performs the required operations (usually based on the content entered by the viewer) and formats the results into a web server and a document that the browser can understand (usually an HTML web page). Finally, the web server returns the results to the browser.
3.1.2 embedded server boa server
Boa Server is a small single-tasking embedded server that supports CGI. The executable code is only about 60 kB. It is small in size, fast in speed, and safe. It can meet the development of this project. The boa server needs to be cross-compiled into programs that can run under the ARM platform. In the pc environment, after cross-compilation of the boa server using the cross compiler arm-linux-gcc, you need to modify its configuration file boa. Conf, the key configuration is to create the directory where the log file is located, create the main directory of the HTML document, save the static web page into the directory, create the directory where the CGI script is located, and store the script of the cgi in the directory.
3.2 background design
When the system is running, the access controller will always run the main monitoring program. The main monitoring program has two working modes, namely debugging mode and monitoring mode.
3.2.1 Debug mode
In the debug mode, you can perform some basic settings on the access controller: including the IP settings of the access controller, the system administrator user name and password settings, and the card permission settings. In this part, you need to cooperate with the graphical environment to facilitate debugging. This system uses minigui embedded graphics library.
Communication under MiniGUI is a message mechanism similar to Win32. It is a free software developed by a company that follows the LGPL protocol and can be a fast, stable and lightweight graphical user interface support system for embedded Linux systems.
3.2.2 Monitoring mode
In the working mode, the daemon monitors whether there is any card information at any time. After detecting the card information, the background program accesses the database to compare the card information. Only when the comparison is passed, the door can be opened. action.
Since the image needs to be saved to the database at the same time as opening the door, at this time, there may be a client accessing the system to store the image, which may cause an access violation to the same database, so the system receives the client access system to store the image request. At the same time, the front-end CGI service program communicates with the background monitor through the inter-process communication method of the named pipe to obtain the database access handle. After the client access ends, the front-end CGI service program releases the database handle.
In this system, due to the frequent database access operations, the ARM9-based hardware platform selects the database as the Berkeley DB database. Berkeley DB is a long-established embedded database system, mainly applied to the UNIX/LINUX operating system. It is simple, compact, reliable and high performance to meet the needs of this system.
2000W Digital Tv Transmitter,Wireless Fm Digital Transmitter,2Kw Wireless Digital Tv Transmitter,2Kw Video Digital Tv Transmitter
Anshan Yuexing Technology Electronics Co., LTD , https://www.yxhtfmtv.com