
Pen Test Partners, a UK-based cybersecurity company focused on penetration testing and security services, recently warned that even with advanced encryption solutions, more than 100 million IoT devices from thousands of vendors are vulnerable to "Z- The impact of a Wave Downgrade Attack, which allows an attacker to gain unauthorized access to a user device.
Z-Wave is a wireless communication protocol for simple, reliable performance and for home automation. It was developed in 2001 by Zensys, a technology company based in Copenhagen, Denmark. US company Sigma Designs completed the acquisition of Z-Wave at Sigma Designs and announced on the 4th and 18th of this year that the Z-Wave business was sold to Silicon Labs for $240 million (also known as "core technology").

Wireless networks based on Z-Wave technology are commonly used for communication between Home Appliances and devices, allowing users to wirelessly control home appliances and other devices through local network devices or the Internet, such as Lighting systems, security alarm systems, and thermostats. , smart locks and garage door openers, etc.
Ken Munro and Andrew TIerney, two security researchers from Pen Test Partners, point out that the latest security standard used by Z-Wave is called the S2 framework, using an advanced anonymous key protocol, the elliptic curve key exchange mechanism. (EllipTIc-CurveDiffie-Hellman, ECDH), sharing a unique network key pairing process between the controller and the client device.
After Silicon Labs took over the Z-Wave business, they forced certified IoT devices to use the latest S2 framework, as the previous S0 framework was confirmed to be a security risk in 2013. The S0 framework uses a hard-coded encryption key (ie, 0000000000000000) to protect the network key, which allows an attacker to intercept communications within the target device and this vulnerability is completely resolved in the S2 framework.
Munro and TIerney found that many IoT devices still support the insecure S0 framework, with the goal of achieving compatibility. But they said that devices that support both frameworks are likely to be forced to downgrade the pairing process from S2 to S0 and name the downgrade attack technology "Z-Shave."
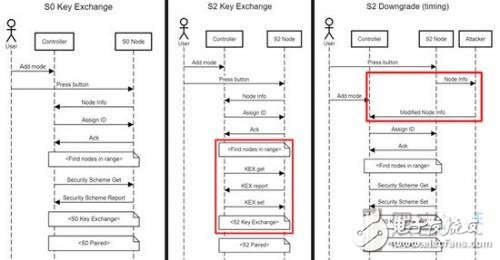
The researchers explained that the nodeinfo command containing the security class is completely unencrypted and not authenticated, allowing an attacker to allow interception or spoofing of commands that do not have a security class node set. This makes it easy for an attacker to intercept a range of key exchanges in the pairing process and obtain a network key that can remotely control the device.
The two researchers tested the Conexis L1 smart door lock during the experiment, a smart door lock made by the British company Yale, which costs about $360. The test results confirmed that they were able to steal the key and gain permanent control over the smart door lock.

The researchers stressed that we should focus our attention on the unsafe S0 framework and the Z-Shave downgrade attack technology, not just the ConexisL1 smart door lock. According to relevant information, as of April 18 this year, a total of 2,400 suppliers of IoT devices use Z-Wave chips, covering a range of products such as door locks, lighting, heaters and home alarms. It is possible to reach more than 100 million units.
Silicon Labs confirmed the results of Pen Test Partners in a blog post last week, but said that such a downgrade attack is almost impossible to achieve in practice. Because launching an attack requires the attacker to physically access the device during the pairing process, and the pairing is done during the initial installation or reinstallation, which needs to be done by the device owner or installation professional, which means that the device owner is trying to attack. Will definitely be on the scene.
Silicon Labs said that although the attacks are difficult to achieve in practice, they still attach great importance to the reports submitted by partner companies. Replacing the S0 framework with the S2 framework completely cannot be completely implemented in the short term because it requires compatibility issues to be resolved. In addition, the company said they are updating the specification to ensure that any user will not only receive a warning when downgrading to S0, but must also select "Receive" before the downgrade will be executed.
SHENZHEN CHONDEKUAI TECHNOLOGY CO.LTD , https://www.szfourinone.com